I'd like to tell you a story. Its a story that doesn't particularly make me look very good. It was at a point in my career where I still had a lot to learn, and like many young people I thought I was smarter than I was. But its a true story and there is an important point to it, so I'm telling it here even at the risk of looking a bit like a schmuck.
To tell the story, we have to go back in time. The year was 2006. There were still movies in the theaters that didn't have a single comic book character in them. George W. Bush was still best known for destroying the middle east and not for his adorable stick-figure self-portraits. No one that worked outside of telecommunications or that didn't wallpaper their house in aluminum foil believed that the NSA was wiretapping everyone and everything. And I had just received a promotion.
I was working within the primary data center of an internet service provider. The company I was working for had a tiered engineering structure and I had just gone from Tier 1 to Tier 2. I would be making more money and accepting more responsibility in return.
A big part of that responsibility was investigating and resolving abuse complaints received by the ISP. Whether a company hosts servers, websites, emails or provides commercial internet service (this company provided all of the above) occasionally someone will do something on your network they aren't supposed to. Sometimes when someone does something naughty on your network, someone from another network notices. Maybe someone downloaded copyrighted material with P2P software and was caught: the copyright holder would send in a DMCA request. Maybe someone's website has been compromised and the hacker has started scanning the entire internet for a specific exploit; the admin of another network notices and sends an email begging to make the scanning stop. Or maybe someone has defrauded the company by using a stolen credit card and fake company details to sign up for a dedicated server, which in turn is used to send spam - one of the many IP reputation services send over an automated email sending examples of the messages. It had become part of my job to read these messages, investigate them where needed and determine how to handle them.
I was really excited about this promotion. When I was younger I had read books like the Cuckoos Egg; now that was going to be my life. But there was a problem: at this point I knew quite a bit about web servers, but not so much about email servers. I knew even less about the even-at-the-time out-of-date and incredibly-proprietary custom qmail cluster that provided an enormous chunk of this company's email. So I started reading.
I read every RFC that referenced the SMTP protocol. Then I read how no one pays any attention to that shit. I read all about qmail. I learned how to read email headers. I learned how to tell when headers were forged and some of the tricks spammers used. I handled my first few dozen cases well and closed them quickly.
But there was a problem. The cases I came across lacked drama. It wasn't like the Cuckoo's Egg. Although in a few cases I might have been able to find out exactly who was responsible for hacking a server or setting up an illegal spam service, there was nothing I could do with that information. Even in the rare circumstance where the person was actually in the United States, what was I going to do? Call 9-11? Call the State Attorney's Office? Call the FBI or the Secret Service? Despite what you might read in the funny papers, law enforcement is not equipped to investigate or prosecute the vast majority of "cybercrime" cases. Victims have no one to call, local, state and Federal police don't want to be involved unless there is a political or regulatory angle, and the most simple hacking case is almost always a mess of jurisdictional SNAFU's. You think Bernie Fife knows how to get a warrant for those Ukrainian VPN logs? (He doesn't.) The fact is, when you read about a criminal computer crime investigation, you are essentially viewing a photograph of Big Foot.
But I desperately wanted to be a White Hat Cyber Cop. I wanted to take down a Cyber Porn ring or a bunch of Russian mobsters (
Russian Business Network was my Moby Dick). But that just wasn't my job. My job was help fix whatever had been broken, to make sure that my customers were able to safely resume doing business as normal, and to maybe make some recommendations to make the next hack a little harder to pull off without making everyone's life miserable.
One day I came across evidence that two servers owned by the same customer had been the source of a substantial amount of malicious network traffic. Somehow (this was a big network) this had been missed up to this point. It had been going on for months. These servers had been used to break into other servers on other networks; VPN tunnels would then be established and spam would be sent through the tunnels. Most of the time it looked like normal ssl traffic.
The more I investigated the situation the more I became convinced this customer was not the victim of these attacks, but was responsible for the attacks. There was no smoking gun, but it in my mind everything in my mind pointed to the customer being the Bad Guy. I spoke to the technician who built the pair of servers for the customer, and the tech remembered the customer had a series of very specific, unusual requests for how the disks were supposed to be partitioned and for how the kernel was to be configured that was similar to how I had seen customers setup a server that could be immediately wiped of any incriminating evidence. I checked out the websites hosted on the servers. The main website - I will never forget this - was an incredibly bare-bones CMS selling decorative rocks. Geodes, crystals, that sort of thing. That might not be so weird for someone with a $2 a month webhosting plan, but this guy had multiple dedicated servers; most of the customers getting servers were insurance companies, universities, doctors offices, military contractors. And this guy. Selling rocks.
I sent the customer several warnings about the hacking; I gave him my best estimation of how he could lock down his server and told him he could hire us to secure it for him. The responses were spotty, and the hacking continued. Eventually, I made the case to management to cancel this customer's service. I was able to get them to agree to my assessment and the customer's account was canceled.
It was almost immediately after that when I realized that I had completely misread the situation.
Sophisticated spammers know how to plan for having their service canceled. Its part of doing business for them. When they sign up for a 1 year contract they know they are only getting a few months of service out of it. Spammers have always been at the forefront of complex unattended installation, continuous data recovery, imaging and virtualization because they have to turn servers up fast and whenever the
banhammer comes down they need to already be activating service at another provider.
When you cancel a spammer's server, they might send an email in asking why they can't reach their host, and when you tell them they've been spamming they will never contact you again. They're prepared, so there is no point in further discussion.
But the customer with the rock website contacted us, and when we told him he had been spamming he was completely devastated. He sent multiple emails. He called everyone at my company he could. It was clear he had no backups, no plan B. The servers were his livelihood. He begged us to reactivate them, at least long enough to make a backup.
I knew I had made a mistake. I was able to work out a compromise in which we built out a new server to replace his two older servers and helped him transfer his data over safely. The story had a happy ending; the customer got a reduced monthly rate, my company got to reduce the power usage in the data center and keep its profit margin the same, and we stopped the hacking. But the happy ending isn't what's important here.
What's important is that I was wrong. When it counted, I was paying more attention to what I wanted to find than I was to what I could find. I made intuitive leaps based on reasoning that didn't support those leaps. I wanted to be Clifford Stoll. I wanted to impress my boss. I wanted to Get the Bad Guys. Perhaps more important than any of these things, I wanted to have The Answer. More compelling than my fantasizes of being a Cyber Cop was my fear of being incompetent. I thought that being competent meant always having the right solution.
I could have done my job more effectively by taking more time to review the evidence, and spending less time trying to "connect" a handful of dots that didn't lead anywhere meaningful. Although the story had a happy ending, it could just as easily have had a terrible ending. What if the downtime I caused that customer destroyed his business?
Over the years I have taken this experience to heart. I've become very reluctant to use intuitive leaps to justify troubleshooting or infosec determinations. Although computing provides us with a rare opportunity to work in a forum in which objective decision making is possible. There are right and wrong answers in computing; but there are also situations in which we don't have enough data to determine the difference between them. Its become easier for me to point out when there isn't enough information to resolve a problem (owning my own business has had no small part in this).
Alright, so that's the story. What on earth does all of this have to do with the DNC hacks?
Over the last week or so I've begun getting my hands on and reviewing the emails and attachments from the
Democratic National Committee that have been leaked to the public by a shadowy figure(s) named Guccifer 2.0. This hack became international news beginning last month when the controversial "cyberwarfare" company Crowdstrike announced that the DNC had been hacked, and shortly afterward documents from the DNC began being leaked to a variety of different news outlets, from the
Smoking Gun to
Wikileaks.
From the very beginning of the DNC hack's injection into the news cycle, the blame for the incident has been squarely laid at the feet of Russian intelligence services. The Russian connection was established by Crowdstrike, who had been asked by the DNC to investigate a hack before the leaks began.
Crowdstrike CTO Dmitri Alperovitch published a public report of the findings of their investigation, apparently at the behest of the DNC, in which samples of malware were provided that had links to other attacks that had already been attributed to Russian intelligence, like
the compromise of the German Bundestag's network discovered earlier this year.
The attribution to Russian intelligence has gained steam over the last few weeks until we reached the point we are at now - where news outlets are now reporting the Russian intelligence attribution as fact. It is primarily this that I take issue with. Please note that it may very well be the case that Russian intelligence is behind all this. My concern is there is not nearly enough evidence to declare that attribution as fact without additional evidence.
Crowdstrike's report does not provide the required evidence to establish the attribution. Although the report provides a malware sample and a list of IP addresses associated with prior Russian intelligence-attributed hacks that Crowdstrike claims to have recovered through their investigation, these samples are provided without any form of context and in a format that makes it impossible for other researchers to attempt to replicate their findings. There is no explanation of how these samples were acquired. This is a bit like if your doctor told you that you have lung cancer, and as evidence offers you a picture of a cancer cell that's been cut out of a medical journal instead of, say, an X-Ray of your chest. The Crowdstrike report is an
explanation of Crowdstrike's findings. It is not
proof of Crowdstrike's findings.
There are a number of reasons why Crowdstrike would have opted the report in a way that cannot be objectively verified or peer reviewed. The first and foremost reason is that the DNC almost certainly asked them not to provide any information about their network. Another possibility (that is less defensible but I hear repeatedly) is that Crowdstrike would not want to reveal their "sources and methods".
And, to be fair, Crowdstrike provided their findings to two other companies - Fidelis, Mandiant and ThreatConnect - all of whom have apparently confirmed at least some of Crowdstrike's findings.
Those who have read the Crowdstrike (or Fedelis) reports may notice that there is a lack of any mention of the DNC's email servers or evidence of large-scale file retrieval. Its quite likely that these details were left out as part of the concerns I listed already - that the DNC hopes to profit from security-through-obscurity and prevent even basic information about their network from going public. Reporters eager to demonstrate the Russian connection have relied primarily on the
@pwnallthethings Twitter feed, maintained by Matt Tait (who, apropos of nothing, claims to have been "an information security specialist for GCHQ").
Tait's Twitter feed has been used to bridge the gap between the Crowdstrike report and the DNC documents leaks by Guccifer 2.0. Tait's primary contribution was discovering that a number of the documents released by Guccifer 2.0 had been modified, and that the individual who made these changes was using a version of Windows with the Russian Language pack enabled. When reporters and bloggers say that "metadata" within the Guccifer 2.0 documents proves a Russian intelligence connection, this is what they are talking about.
In addition to this finding, journalists relied on retweets from Tait's Twitter account for confirmation of other findings, such as the Bundestag link, as illustrated here:
As I was reading through Tait's tweets and his subsequent
blog guest posts, I saw myself 10 years ago, with the rock reseller. The DNC hacks significantly increased Tait's cache on social media, as can be seen here (the hack became public June 14th).
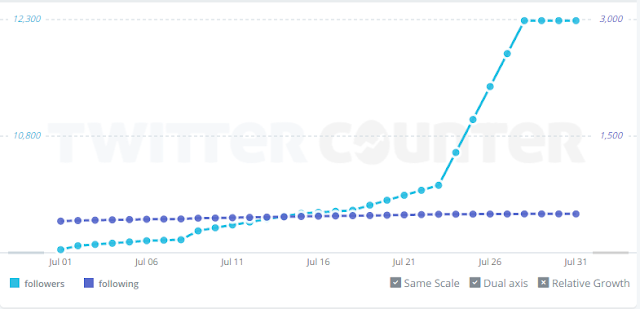 |
| @pwnallthethings follower growth for July 2016 |
Just to be clear: I'm not alleging some sort of a conspiracy. I didn't accuse the rock seller of being a spammer because I hated him and wanted to get him. I went after him because it was
a better story than the truth. It was
more interesting than the truth. And there
was evidence that confirmed my story, just as there is evidence pointing toward Russian Intelligence being behind the DNC leaks. Its just not enough evidence for us to claim it as a fact (yet).
Tait rejects the claim that his findings are influenced by bias:
Seems reasonable. But the trouble is that everyone is biased. I'm biased. You're biased. If you are human, and you have a subjective point of view of consciousness, you are biased. The way to handle this is not to deny it, but to account for it. I don't think Tait or the journalists who have used his findings as definitive proof that "Russians did it" have a bone to pick with Russia. Its just a damn good story. Who wouldn't want to be part of a spy novel?
Also, I use Tait here because the media has decided to rely on his findings so consistently, but he is not alone in transforming tenuous circumstantial findings into Objective Truth. Some of my personal favorites are:
- Vice Magazine
brought in linguists (I am very much avoiding the use of a hackneyed but still-amusing pun here) to analyze the transcript of an interview between a Vice reporter and Guccifer 2.0. Even the honey-picked quotes provided by Vice made it clear that nothing could be proved from these transcripts other than that Guccifer 2.0 likely used Google Translate, but the article has been used as further "proof" that Guccifer 2.0 is Russian and not Romanian.
- The version of MS Office used to modify leaked files appears to be cracked. Cracked versions of Office are "popular among Russians and Romanians". Because no one anywhere else in the world pirates Microsoft software (certainly I don't - stop looking at my torrents).
This is just silly, but its taken as gospel by a media that is both hungry to spark a Cyber War and whose reporters frequently have the technical acumen of my 94 year old grandmother.
So before we wrap this post up lets quickly review the fallacies that are used to confirm the Russian Connection:
THE RUSSIANS HACKED THE DNC, SO THE DNC LEAKS CAME FROM THE RUSSIANSThis is the big one. As I said earlier, I am taking for granted that Crowdstrike's report is God's Own Truth, and that a pair of separate Russian intelligence services hacked the DNC and had access to the DNC's network for up to a year.
Even if we accept that Russian Intelligence hacked the DNC, it does not mean that Russian Intelligence leaked the documents. Let's consider some scenarios.
The number 1 reason why networks and servers are compromised is because those networks / servers are vulnerable to compromise. That's such an obvious statement it comes across as a tautology. But its not, and there are important consequences of this obvious statement. I am regularly called in to help companies that have discovered a breach in their IT infrastructure. Something that often happens is I find evidence of multiple compromises; either the victim is using multiple vulnerable software packages, or multiple parties have taken advantage of the same exploit, or the network was compromised a long time ago by a clever hacker who was able to maintain a presence on the network until some much-less-competent hacker came along and defaced a website or broke something.
One of the most compelling alternate explanations relies on a similar chain of events happening at the DNC. Russian intelligence had compromised the DNC for a long time using the sophisticated techniques described by CrowdStrike. The Russians stayed present in the network for a year in order to accomplish what intelligence services typically want to accomplish - compiling as much information as possible. Then, some knucklehead(s) named Guccifer 2.0 comes along and compromises an email server with the goal of accomplishing some hare-brained political goals known only to him/them. Guccifer 2.0, being a moron, sets off the bells and whistles that cause the DNC to contact CrowdStrike, who in turn discover the Russian intelligence presence.
There's other options. Remember that guy name Edward Snowden? Remember how he worked for a US intelligence agency? Remember how he leaked a bunch of documents to the media? Remember this other person Chelsea Manning? Remember how Chelsea released all of those cables that included detailed intelligence analyses of foreign countries? Remember how those documents had huge political implications in those countries, like maybe sparking the Arab Spring? The point is that leaks within intelligence services happen that aren't necessarily planned by that intelligence service. Those leaks can have devastating impacts on the elections of foreign countries. Here, Guccifer 2.0 is either a Russian intelligence employee or a hacker whose true target was Russian intelligence. Theres a few options within this option - Guccifer 2.0 as working for another nation hoping to influence the US election and increasing US/Russian tensions, Guccifer 2.0 as a Russian intelligence employee who has for whatever reason a *huuuuuuuuuge* (get it?) man-crush on Trump. Some of these options are crazy. But its no more crazy than the explanations of the Putin-Trump Axis of Evil floating through the media.
EVERYONE WHO SPEAKS RUSSIAN WORKS FOR THE GRU/FSB
It sounds silly when its put into words, doesn't it? But this is what the "metadata" and "language analysis" comes down to. Guccifer 2.0 is using Office with Russian language settings. Guccifer 2.0 is chatting the way a Russian would chat. ERGO Guccifer 2.0 is Russian. ERGO Guccifer 2.0 is really Russian Intelligence. I'm not sure how to explain how stupid this is, other than to just point out that, no, not everyone who speaks Russian is a GRU agent. Maybe visit Russia and meet some of them? There are some people who speak Russian who are butchers and bakers and candlestick makers. By golly, there are even people who speak Russian that
don't live in Russia at all! I know, your mind is blown, right?
EVERY POLITICAL HACK IS STATE SPONSOREDNot every hacker is state-sponsored. Gee whiz, there are even *groups* of hackers who *cooperate* with each other and even *manipulate the media* and *lie about their identity* who are just teenagers somewhere. There is a rich, long standing history of teenagers playing such pranks. Kids have been hacking for longer and frequently using more sophisticated techniques than governments have. Some of the first government "cyber warfare" programs were just field agents who paid kids to hack for them and paid them in drugs.
Really.
One of the most recent, well known examples of this is the lulzsec hacking group. lulzsec had a very pointed political agenda and targeted government agencies, law enforcement groups, media companies and others that opposed that agenda. The lulzsec political agenda did not fall into the binary Team Red / Team Blue archetypes that inform what passes for American political commentary, but it was there and it clearly was important to lulzsec and their supporters. Before the indictments began, there were plenty of rumors that lulzsec was state-sponsored.
If you've made it this far - congratulations. You're almost at the end. Let's wrap up.
Some companies tell us that there is evidence the DNC was hacked by Russian intelligence. That evidence hasn't been published. There is different evidence that Russian intelligence is behind the Guccifer 2.0 account. Most of that evidence turns out to be at best incredibly flimsy and circumstantial and at worst utterly irrelevant.
It may very well be the case that Russian intelligence is responsible for the DNC email leaks, but the fact remains that further investigation is required to confirm the identity of Guccifer 2.0. Attributing the attacks to the Russians before such an investigation can occur does an enormous dis-service. The Cold War actually completely sucked. We should avoid repeating that experience based on the flimsy BS that has largely informed the coverage of the DNC hacks up to this point.